Industry News
LoRaWAN's Technical Principle and Application in Water Electricity and Gas
With the gradual development of the Internet of Things, many IoT applications have small data packets and high tolerance for latency, requiring widespread deployment. Or it may be located in remote, basement, underground or other heavily shielded locations, where the transmission signals of existing wireless or mobile communication technologies are difficult to reach. The communication technology with long-distance and low power consumption developed in response to the above situation is collectively referred to as Low Power Wide Area Network (LPWAN).
Due to its advantages of low power consumption, long distance, and ultra large connections, LPWAN is suitable for applications that require large-scale deployment and small data transmission. This feature is very in line with the application requirements of intelligent energy meter information collection. LPWAN can be divided into two camps based on its usage frequency band: authorized frequency band and non authorized frequency band. The unauthorized frequency band LPWAN technology developed earlier, with the main technology being LoRaWAN.
I. LoRaWAN Introduction
LoRaWAN is a set of communication protocols and system architecture designed for LoRa long-distance communication networks. It defines how data is transmitted in the LoRaWAN network (where the network refers to nodes, gateways, and servers), defines the types of messages,data frame structures, and security encryption methods. And it introduced the specific operation of network access and explained the difference between the master and slave computers.
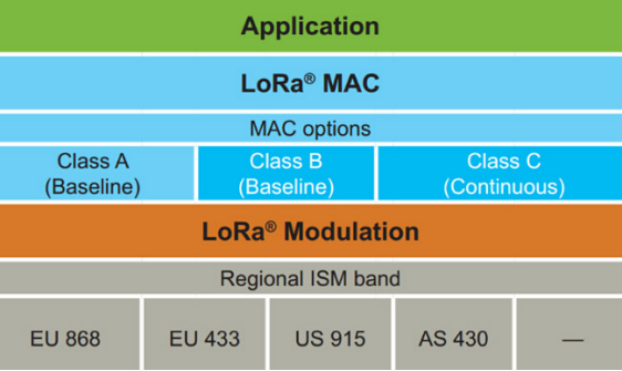
In the design of the protocol and network architecture of LoRaWAN, several factors such as node power consumption, network capacity, security and network application diversity are fully considered.
2. LoRaWAN Network Architecture
The following is the network architecture diagram of LoRa:
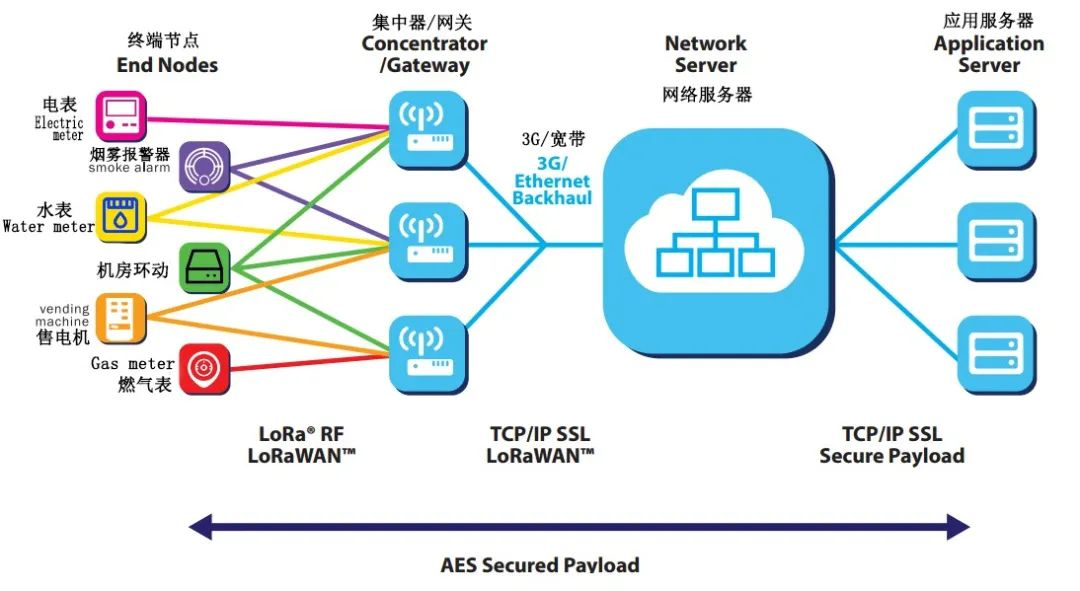
A LoRaWAN network architecture includes four parts: terminal, gateway, network server, and application server. The gateway and terminals adopt star and cellular network topologies, and due to the long-distance nature of LoRa, single hop transmission can be used between them. The terminal node can send to multiple gateways simultaneously, and the gateway forwards the LoRaWAN protocol data between the NS and the terminal. The LoRaWAN data is transmitted between the terminal and gateway through LoRa RF, and through between the gateway and the network server through TCP/IP protocol.
3. Overview of the LoRaWAN protocol
1. Classification of terminal nodes
In terms of technical specifications, the LoRaWAN transmission rate is about 30bit/s-50kbit/s, and the transmission distance is about 2-5 kilometers in urban areas, with a maximum length of 15 kilometers in suburban areas. Supports bidirectional transmission, and the transmission methods can be divided into three levels based on latency requirements and power consumption: Baseline (Class A), Beacon (Class B), and Continuous (Class C). Class A mode only transmits when the terminal device sends a request, with the lowest power consumption, and is applied in water and gas meters. Class C refers to the continuous transmission of data. The transmission delay time is the shortest, and Class C is generally used in electricity meters.
2. Uplink and downlink transmission of terminal nodes
This is the sequence diagram of Class A uplink and downlink . At present, the receiving window RX1 generally starts 1 second after the uplink, while the receiving window RX2 starts 2 seconds after the uplink.
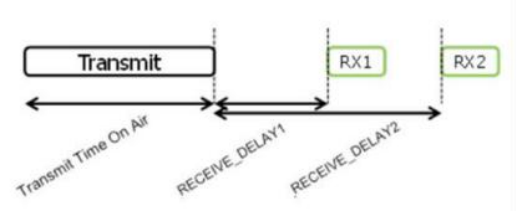
Class C and A are basically the same. During the sleep period of Class A, Class C opened the receive window RX2.
3. Networking of terminal nodes
There are two networking methods for terminal access: Over the Air Activation (OTAA) and Activation by Personalization (ABP).
Commercial LoRaWAN networks generally follow the OTAA activation process to ensure security. This method requires the preparation of DevEUI, AppEUI, and AppKey parameters.

DevEUI is a globally unique ID similar to IEEE EUI64, identifying a unique terminal device. Equivalent to the MAC address of the device.
AppEUI is a globally unique ID similar to IEEE EUI64, identifying a unique application provider..
AppKey is assigned to the terminal by the application owner and needs to be configured on the network server, while being copied on the corresponding terminal.
The terminal issues a join network command after initiating the join network process. After the NS confirms that there are no errors, it will provide a network reply to the terminal and assign the network address DevAddr (32-bit ID).
Both parties use the relevant information in the join network reply process and AppKey to generate session keys NwkSKey and AppSKey, which are used to encrypt and verify for data. Among them, NwkSKey is stored on a network server for communication between the network server and the terminal. AppSKey is stored in the application service provider for communication with network servers.
If the second screening method is used, namely ABP activation. Directly configure the three parameters for the LoRaWAN final communication of DevAddr, NwkSKey, and AppSKey, eliminating the need for a join process. In this case, this device can directly send application data. This situation, due to the lack of bidirectional authentication, may lead to illegal terminal access to the network or the terminal being induced by a pseudo base station. Therefore, in general, commercial projects use the OTAA activation process.
4. Data transmission and reception
After entering the network, the application data is encrypted using the AES128 bit encryption algorithm. The following figure is a schematic diagram of the security mechanisms of various parts in the communication process:
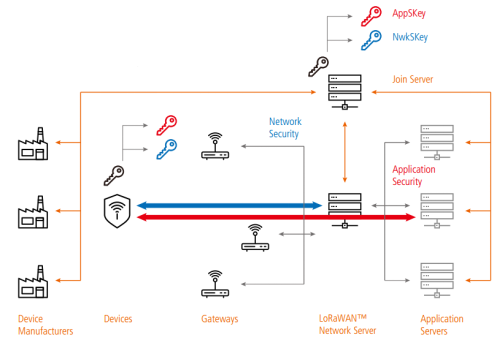
Network servers and terminal nodes use MIC verification to ensure accuracy. MIC verification uses the AES-CMAC algorithm, incorporating frame counting (to prevent retransmission attacks) and NwkSKey (to prevent packet tampering) into the calculation elements. AppSKey is used to encrypt and encrypt user data (as shown in the following figure).
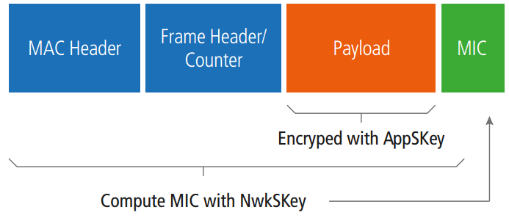
LoRaWAN has two types of specified data frames: Confirmed or Unconfirmed, which are the type that requires a response and the type that does not require a response. Manufacturers can choose appropriate types based on application needs.
Additionally, from the introduction, it can be seen that a major consideration in the initial design of LoRaWAN was to support application diversity. In addition to using AppEUI to partition applications. During transmission, the FPort application port can also be used to process data respectively. The value range of FPort is (1-223), specified by the application layer.
5. ADR mechanism
There are spreading spectrum factor in LoRa modulation. Different spreading factors have different transmission distances and rates, and do not affect each other's data transmission.
In order to expand the capacity of the LoRaWAN network, a LoRa Adaptive Data Rate-ADR mechanism was designed on the protocol. Devices with different transmission distances will use the fastest data rate possible according to the transmission status. This also makes the overall data transmission more efficient.
4. LoRaWAN Characteristic
LoRaWAN is characterized by wireless transmission, strong anti-interference ability, encrypted communication, wide coverage, low power consumption, large connection and low cost.
Long distance: Thanks to the gain of spread spectrum modulation and forward error correction code, LoRa achieves about twice the communication distance of cellular technology.
Large capacity: There are many nodes in the Internet of Things. A LoRaWAN network can easily connect tens of thousands of nodes.
Easy capacity expansion: When a LoRaWAN network needs to increase capacity, you can add gateways.
Security: LoRaWAN is a double encrypted Internet of Things.It is suitable for information application of water and electricity meters.
5. Technical indicators of gateway and module
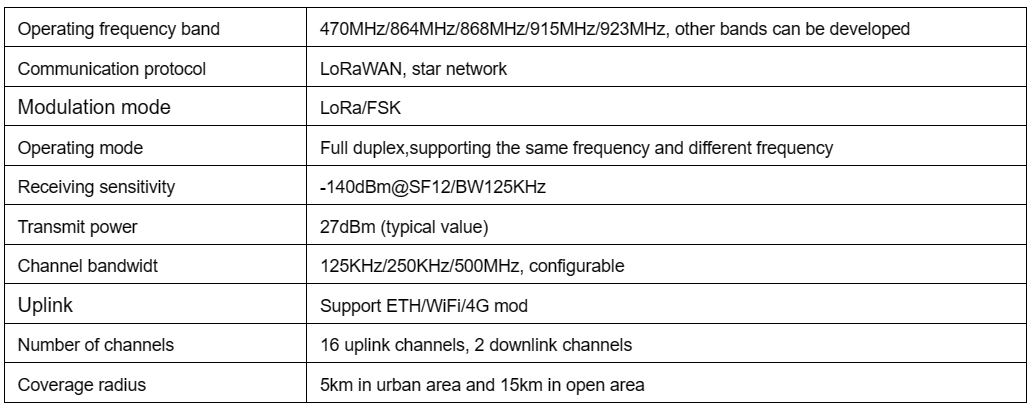
1.gateway

Intelligent gateway G200 (indoor)


Intelligent gateway G500 (outdoor)
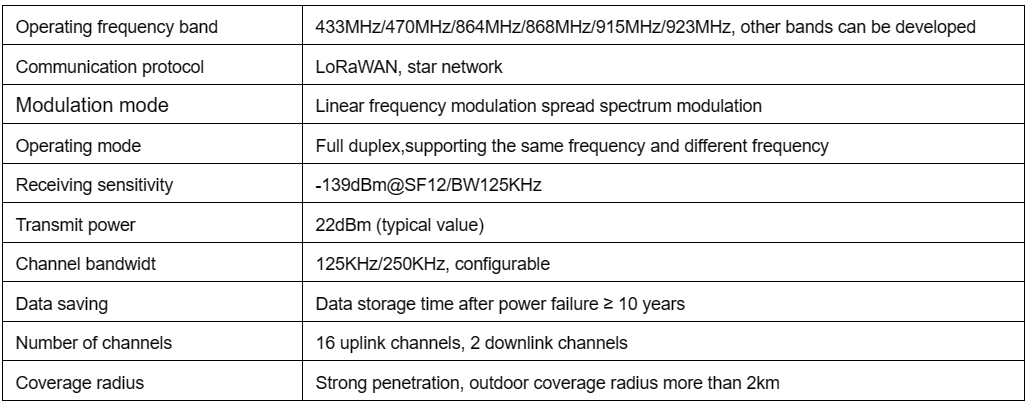
2. LoRaWan module









 Online service
Online service

 Hotline
Hotline

 WhatsApp
WhatsApp
